Quick Summary
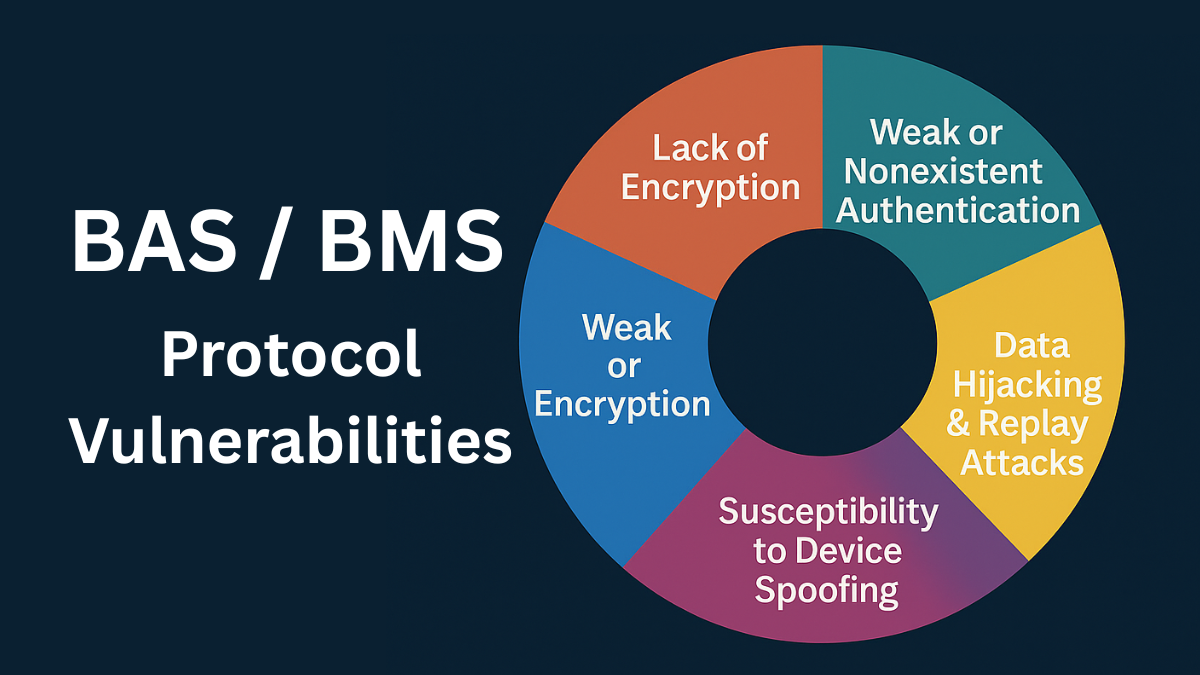
Legacy BAS/BMS protocols share common vulnerabilities, including no encryption, weak authentication, spoofing risks, replay attacks, and weak access controls. These flaws expose HVAC, lighting, and access systems to manipulation and disruption. Zero Trust, encryption, and device-level authentication can secure even legacy systems without costly replacement.
Introduction
Building automation systems (BAS) connect and control HVAC, lighting, access control, elevators, and energy management systems. To enable this interoperability, a variety of communication protocols, such as BACnet, Modbus, KNX, and LonWorks, have been widely adopted across industries.
The challenge is that these protocols were developed decades ago, long before cybersecurity was a consideration. They were designed for reliability and efficiency, not resilience against cyberattacks. As a result, they share a common set of weaknesses that attackers can exploit to disrupt operations, steal data, or even use BAS as a stepping stone into corporate IT networks.
This article outlines five protocol vulnerabilities that affect nearly all legacy BAS protocols and provides guidance on how to address them.
-
Lack of Encryption
Most BAS protocols transmit data in plaintext. This means commands, setpoints, and sensor readings can be intercepted or altered during transmission.
- Risk: Attackers can eavesdrop on sensitive operational data, learn intelligence from building meta-data, or inject malicious commands.
- Impact: Compromised data integrity, false alarms, or operational disruption.
-
Weak or Nonexistent Authentication
Many building protocols were designed with the assumption that all devices on the network are trusted. They often lack strong authentication mechanisms.
- Risk: Any device that connects can send commands as if it were legitimate.
- Impact: Device spoofing, unauthorized control of HVAC, lighting, or access systems, and exposure to insider threats.
-
Susceptibility to Device Spoofing
Without cryptographic identity validation, attackers can impersonate trusted devices or controllers.
- Risk: A malicious actor could masquerade as a building controller, issuing harmful commands or falsifying sensor data.
- Impact: Disrupted operations, safety hazards, and difficulty detecting the intrusion.
-
Data Hijacking and Replay Attacks
Protocols that lack session validation are vulnerable to replay attacks — where attackers capture legitimate data packets and resend them later to cause disruption.
- Risk: Even if the commands are authentic, replaying them at the wrong time can disable systems or create dangerous conditions.
- Impact: Shutdowns of HVAC, energy distribution, or access control systems.
-
Weak Access Controls
Many BAS protocols offer limited role-based access, relying on default or weak credentials.
- Risk: Attackers or unauthorized insiders can gain elevated privileges.
- Impact: Full administrative control over building systems, allowing for mass disruption or long-term persistence.
Why These Vulnerabilities Matter
Because these weaknesses are common across multiple BAS protocols, they represent systemic risks. Firewalls and network segmentation can reduce exposure, but once an attacker breaches the perimeter, these protocol flaws allow lateral movement and deep compromise of building systems.
Attackers are aware of these gaps — and as buildings become more connected to cloud services and enterprise IT, the attack surface grows.
Mitigation Strategies
Facility managers and operators can take concrete steps to address these vulnerabilities:
- Adopt Zero Trust: Verify every device and transaction instead of assuming trust within the network.
- Encrypt Communications: Protect data from interception and tampering.
- Enforce Device-Level Authentication: Assign cryptographic identities to all devices.
- Retrofit Security for Legacy Devices: Solutions like Veridify’s DOME™ platform add authentication and encryption without replacing equipment.
- Implement Continuous Monitoring: Detect anomalies, spoofing attempts, or replayed commands in real time.
Conclusion
Protocols like BACnet, Modbus, KNX, and LonWorks are the backbone of modern building automation, but they were never built to withstand today’s cyber threats. Their shared vulnerabilities, lack of encryption, poor authentication, device spoofing, replay attacks, and weak access controls, make them a prime target for attackers.
By embracing Zero Trust, device-level protection, and retrofit solutions, building owners can secure critical infrastructure without costly system overhauls. It’s no longer enough to assume trust inside the building network — security must be enforced at every connection.
Key Takeaways
- Most BAS protocols were designed before cybersecurity was a priority.
- Five common vulnerabilities impact nearly all:
- Lack of encryption
- Weak authentication
- Device spoofing
- Replay/data hijacking
- Weak access controls
- Firewalls and segmentation alone are insufficient once attackers get inside the network.
- Zero Trust and device-level security provide lasting resilience.
- Retrofit solutions like DOME™ secure legacy BAS without requiring hardware replacement.
—
Blog Post Summary – All of our posts listed on one page


