Modbus Overview
The Modbus protocol, a cornerstone of industrial control systems (ICS), has long served as a fundamental means for communication in critical infrastructure environments, such as manufacturing, energy, and water treatment. However, the growing interconnectivity of these systems with the broader IT landscape and the evolving threat landscape have underscored the pressing need for enhanced security measures.
Modbus, in its traditional form, often lacks robust authentication, encryption, and access controls, making it susceptible to a wide range of cybersecurity risks. Without adequate protection, malicious actors can exploit vulnerabilities in Modbus implementations to disrupt industrial processes, compromise sensitive data, and even jeopardize public safety. As the importance of secure and resilient ICS systems continues to grow, addressing the security needs of Modbus is a critical imperative in safeguarding our critical infrastructure.
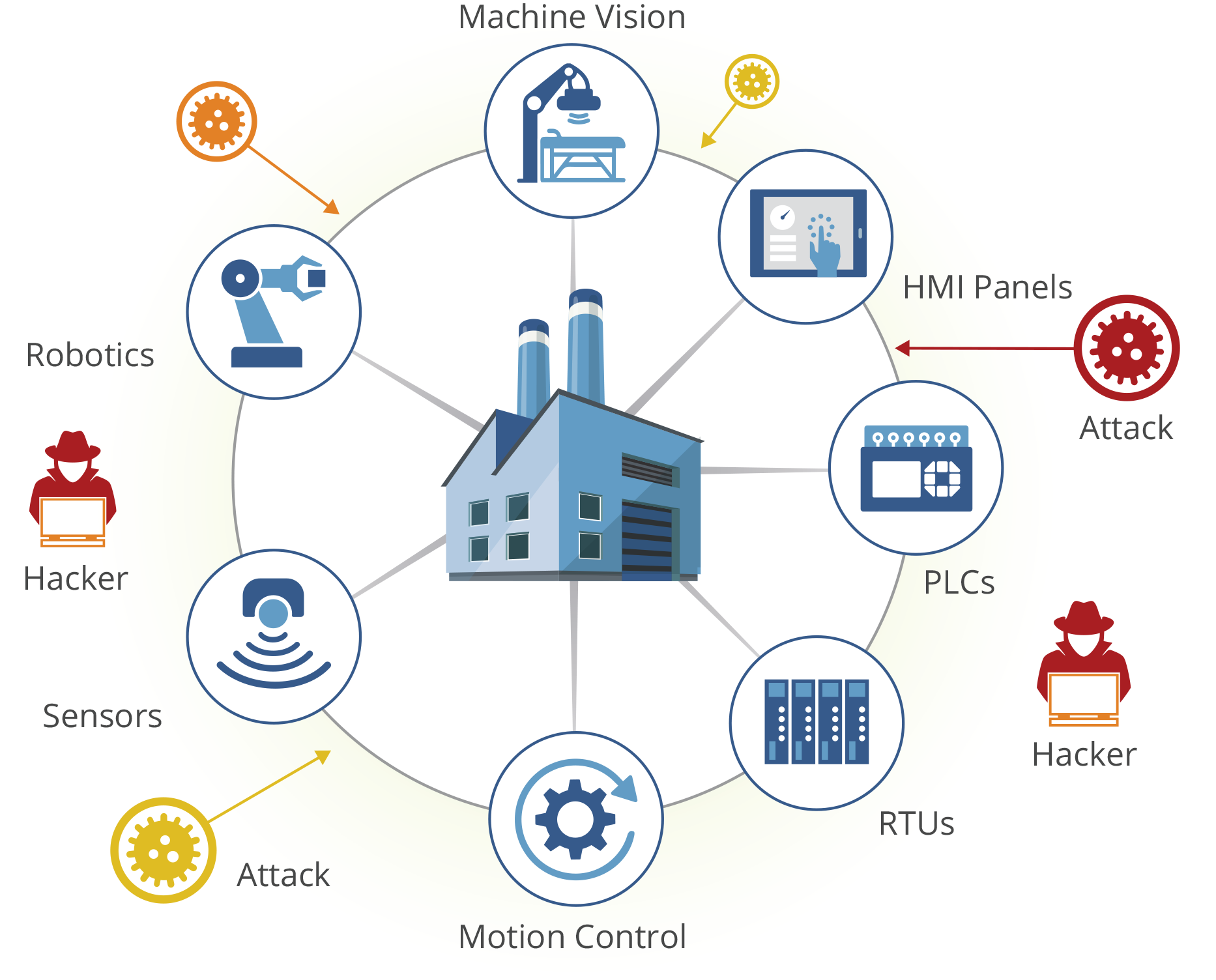
Key Cybersecurity Risks Associated with Modbus:
- Lack of Authentication: Modbus TCP typically lacks robust authentication mechanisms, making it vulnerable to unauthorized access. Attackers can easily intercept and manipulate data if they gain access to the network.
- No Encryption: Data transmitted over Modbus TCP is usually not encrypted. This means that any data sent between devices is exposed and can be intercepted and exploited by malicious actors.
- Vulnerability to Eavesdropping: Modbus TCP communication is often unencrypted and in plain text, which allows attackers to eavesdrop on the data flow, potentially gaining insights into system operations and control commands.
- Device Vulnerabilities: Many legacy ICS devices using Modbus TCP were not designed with security in mind and may contain known vulnerabilities that can be exploited by attackers.
- Man-in-the-Middle Attacks: Attackers can potentially intercept Modbus TCP communications and inject malicious data or commands, leading to process disruptions, data corruption, or damage to critical infrastructure.
- Scanning and Enumeration: Attackers may perform network scans to discover Modbus TCP devices on the network and use this information to target specific systems for exploitation.
- Injection Attacks: Malicious data or commands can be injected into Modbus TCP communications, potentially causing disruption, damage, or unauthorized control of industrial processes.
- Legacy Systems: Many Modbus TCP systems are part of legacy infrastructure, making them challenging to update or secure adequately due to compatibility and operational considerations.
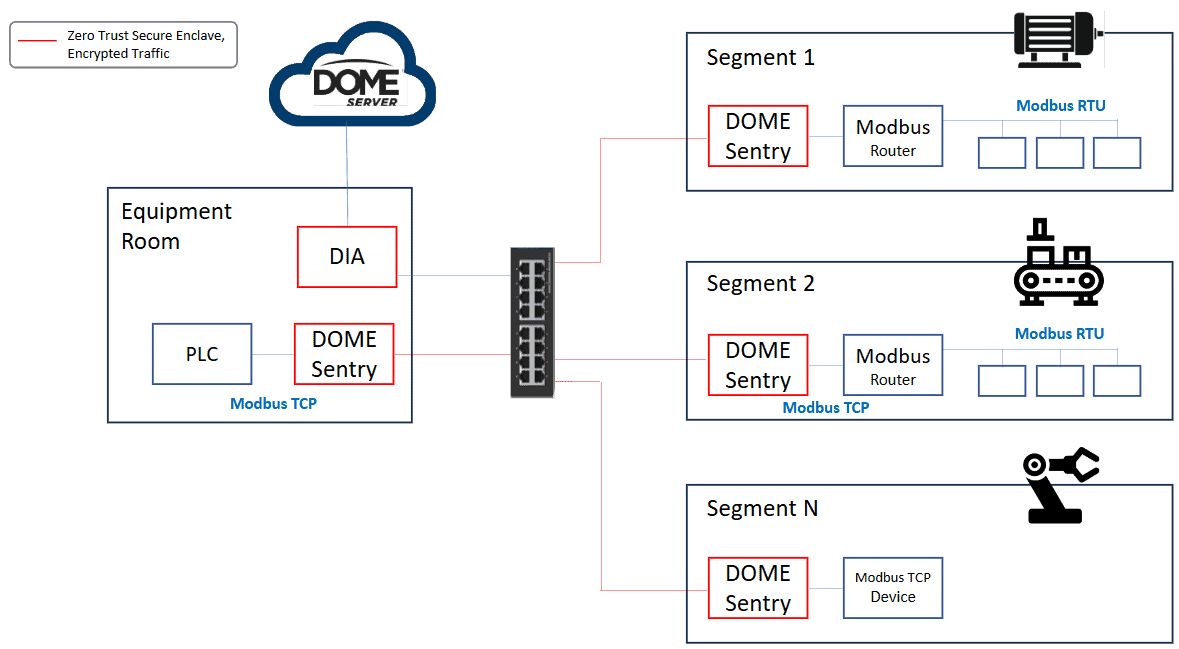
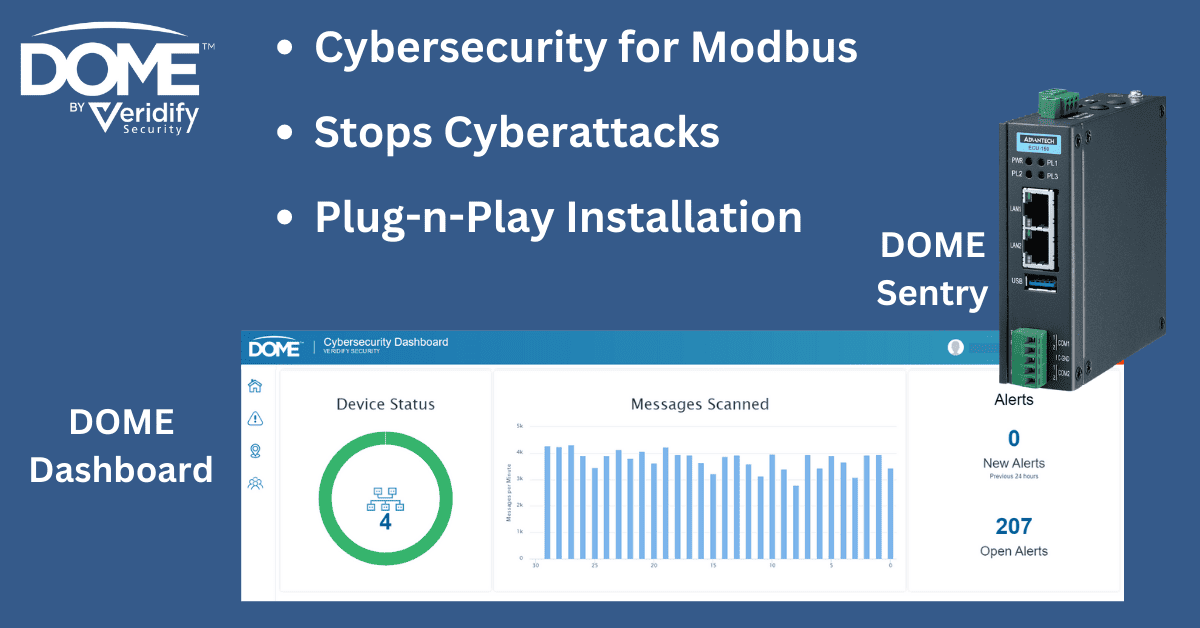
Increase OT Security for Modbus Systems with DOME
Veridify’s DOME platform provides several key security measures:
- Provides security for existing Modbus devices – Modbus TCP and Modbus RTU
- Provides mutual authentication between devices
- Uses a NIST-compliant Zero-Trust framework to block all communications from un-authenticated devices
- Established secure communication tunnels and encrypts all traffic
- Protects existing, installed devices
- No changes to the network or topology
- No IT/cyber skills are needed - installs in minutes using existing technicians
- Automatically manages security certificates and renewal – typically a difficult process