Zero Trust OT Security Made Easy
Device-Level
OT Security
Real-Time Cyber Defense to the Edge for OT Devices
Protect Existing
OT Networks
Authentication and Encryption for Existing OT Devices
Easy to Install
and Operate
No Cyber or IT Skills Needed, use Existing Technicians
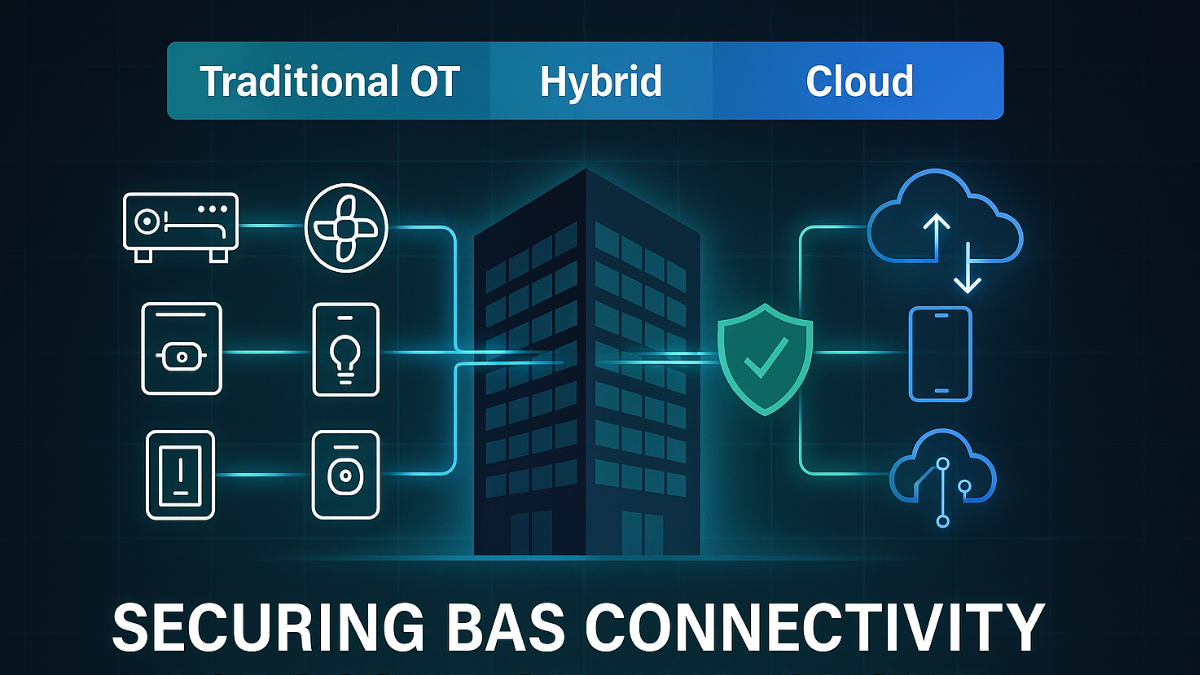
Building Automation
Cybersecurity for Building Automation Controls and Smart Buildings
Endpoint Protection for Industrial Automation, ICS, OT, SCADA Devices
Cybersecurity for Critical Infrastructure Controls and Endpoints

Zero Trust Security for Operational Technology (OT) and IoT Devices
• Root-of-Trust Secured in a Blockchain
• Device Authentication
• Enforce Device Communication Policies
• Real-Time Cyberattack Prevention
OT Security and Building Automation Cybersecruity Partners
Key Benefits of Veridify’s DOME Platform

Device Protection Inside the Firewall
Body Armor for Your OT Devices: We protect your automation control devices, equipment, and machines from even inside-the-perimeter attacks without the need for complicated network segmentation or microsegmentation.

Real-Time Cyber Defense
Proactive Defense: We stop cyberattacks on your devices in real-time. Other “monitoring” solutions just tell you there might be a problem that someone then has to analyze, investigate, and remediate.
Universal Compatibility
Any Device, Any Age: We protect new, existing, and legacy devices. The age of the automation control device or firmware version does not matter. If it’s operational, we can protect it.

Plug & Play – No Cyber or IT Expertise Needed
Zero Trust Protection in Minutes, Not Months: We can secure your automation control devices without the need for costly and overburdened IT or Cyber staff. You can use your existing technicians to deploy and manage real-time OT security.
Recent Blog Articles
Insight for IoT, Smart Building, & OT Security
Featured Resources