Search results for: operational technology
Quantum-Resistant Security for IoT and M2M Devices
Imagine a lock that’s been guarding your front door for decades. It’s served you well, but now thieves have invented high-tech tools that can pick it in seconds. As quantum computing advances this is the challenge facing today’s encryption methods, including those used by Internet of Things (IoT) and Machine-to-Machine (M2M) devices – from smart…
Read MoreSecuring Critical Infrastructure to Reduce OT Cyber Risks and Impacts
Webinar Summary – Securing Critical Infrastructure (OT) In the webinar about securing critical infrastructure hosted by KMC Controls, the panelists discussed critical infrastructure and the importance of hardening operational technology (OT) against cyber vulnerabilities. The session featured insights from Sandy Kline, Louis Parks, and Paris Stringfellow, who shared their extensive experience in cybersecurity and operational…
Read MoreVeridify Enhances DOME Sentry Cybersecurity with Multi-Protocol Model
Closes critical cyber protection gap between Operational Technology and Managed Services on shared Building Networks Shelton, CT (January 14, 2025) — Veridify Security, the leading provider of device-level cybersecurity solutions for building automation and industrial controls, today announced multi-protocol enhancements for the DOME Sentry™. With this software release, the DOME Sentry will now provide NIST Zero…
Read MoreEU NIS2 Directive and Implications for BAS-BMS Cybersecurity
The EU NIS2 Directive (Network and Information Security 2 Directive), which replaces the original NIS Directive, aims to strengthen cybersecurity requirements across critical sectors, including energy, healthcare, transportation, and digital infrastructure. While not explicitly focused on building automation systems (BAS), its implications for such systems are significant, particularly for facilities considered critical infrastructure. Key Implications…
Read MoreBuilding Automation Endpoint Protection Is Critical for Cybersecurity
Building automation systems (BAS), now highly-connected to the internet, have transformed how the infrastructure of residential, commercial, and industrial properties is managed and optimized. From heating, ventilation, and air conditioning (HVAC) systems to lighting, security, life safety, and power distribution, these systems are now smart, centralized, and increasingly automated. While this level of convenience and…
Read MoreBACnet Secure Connect
BACnet Secure Connect (BACnet/SC) and BAS / BMS Cybersecurity BACnet Security Challenges BACnet started as a serial-based protocol and building operational technology (OT) systems were generally not connected to other systems inside or outside of the building. Therefore, there was no security built into the protocol and the messages were plain text. The BACnet standard…
Read MoreModbus Vulnerabilities Used for Cyberattack on a Heating Utility
Heat and Hot Water Disrupted to over 600 buildings, about 100,000 people, for 48 Hours Cyberattack on a Heating Utility A cyberattack on a heating utility (also known as district heating) in the Ukrainian city of Lviv, the largest city in western Ukraine, in January 2024. The malware, named FrostyGoop, is one of the few…
Read MoreProtecting Building OT Systems from Cyber Threats
Operational Technology (OT) systems in buildings, which include HVAC, lighting, access control, and other critical infrastructure, are increasingly becoming targets for cyber threats. The rise in attacks on these systems underscores the importance of robust cybersecurity measures to protect them. Here’s a look at how to safeguard building OT systems from cyber threats. Understanding the…
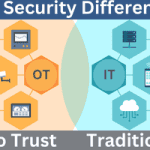
Read MoreKey Differences Between Zero Trust OT Security and Traditional IT Security
How is Zero Trust for OT Security Different from Traditional IT Security? Zero Trust for operational technology (OT) security differs significantly from traditional IT security models in several ways. Here are some key differences: Security Method Traditional IT Security Zero Trust OT Security Trust Model – Assumes that everything inside the network can be trusted.…
Read MoreBrochures
Brochures Veridify Security brochures and marketing collateral for Zero Trust OT Cybersecurity Smart Buildings / Commercial Real Estate Commercial Real Estate Brochure Mitigating Cyber Risks in Operational Technology, Buildings, and Critical Infrastructure Solution Brief Cybersecurity for Building Automation and Smart Facilities eBook Cybersecurity Solution for Smart Buildings eBook Manhattan Office Building Case Study Education…
Read More