Why Building Automation Systems Are the New Cybersecurity Target
Quick Summary
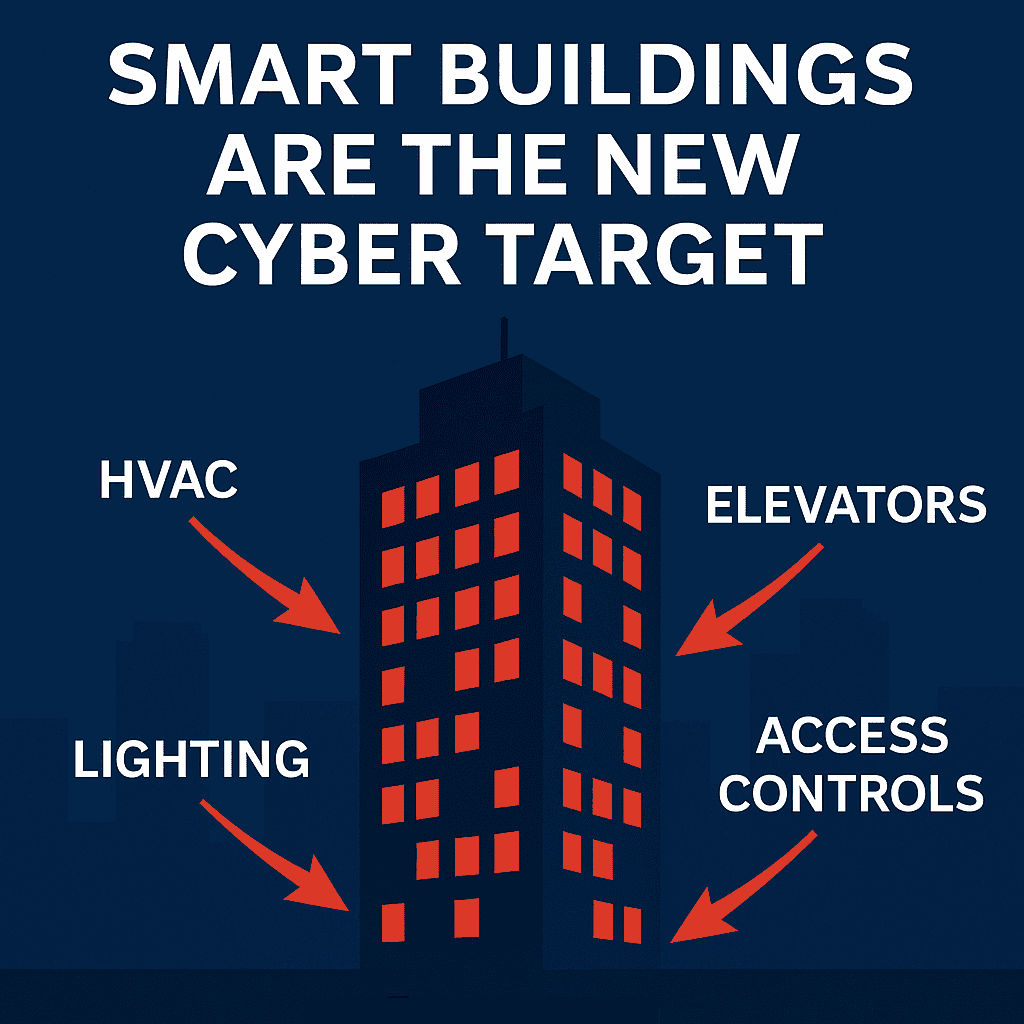
Building Automation Systems (BAS) are increasingly targeted by cybercriminals because they manage critical building functions such as HVAC, lighting, elevators, and access controls. Once considered safe due to isolation, BAS are now internet-connected and often insecure by design, making them gateways to both operational disruption and corporate IT networks. As cyberattacks on smart buildings grow, adopting Zero Trust security at the device level is essential to ensure resilience, compliance, and tenant safety.
Introduction
In recent years, cybercriminals have expanded their focus beyond traditional IT environments and into the realm of operational technology (OT). Among the most vulnerable and high-value targets are Building Automation Systems (BAS), the technologies that control HVAC, lighting, elevators, access controls, and other critical infrastructure within smart buildings. These systems were designed for reliability and operational efficiency, not for cybersecurity. Yet today, they represent an attractive target for attackers seeking to disrupt operations, extort ransoms, or gain access into corporate IT networks.
This article explores why BAS have become a top cybersecurity target, what risks they introduce, and why building owners and facility managers need to take action now.
The Expanding Role of BAS in Smart Buildings
Modern smart buildings rely heavily on BAS to reduce energy costs, improve occupant comfort, and streamline operations. With remote management and integration into cloud-based platforms, BAS is no longer confined to isolated control rooms — it’s connected to enterprise networks and even vendor portals.
This expanded connectivity has created new efficiencies but has also eliminated the “air gap” that once protected building systems. Where once a physical presence was required to access BAS, today attackers can probe vulnerabilities from anywhere in the world.
Why Attackers Target BAS
There are several reasons cybercriminals see BAS as lucrative targets:
- Operational Disruption – Shutting down HVAC systems in a hospital, disabling lighting in a school, or locking elevators in an office tower can cause immediate chaos. Attackers know that downtime in building systems has direct consequences for safety and productivity.
- Pathway into IT Networks – BAS devices often connect to the same networks as corporate IT systems. A compromised BAS controller can become a backdoor into sensitive business applications or data centers.
- Weak Security by Design – Protocols like BACnet and Modbus were never designed with cybersecurity in mind. Many devices still use default credentials, no encryption, and no authentication between devices.
- Attractive to Ransomware Groups – Ransomware operators are increasingly targeting organizations where downtime is intolerable. Shutting down a smart building forces management to respond quickly — making them more likely to pay a ransom.
Real-World Incidents
The shift from theory to reality is already here. Recent cases have shown that attackers are willing to target building systems:
- A U.S. school district was forced to shut down its HVAC systems after attackers disabled BAS controllers, leaving buildings unusable until ransom demands were met (2022).
- The Aliquippa, PA water utility saw its booster station compromised, disrupting critical infrastructure tied to municipal safety (2023).
- Commercial real estate companies have reported access control breaches where attackers locked or unlocked doors remotely.
These incidents underscore a sobering truth: BAS cyberattacks are no longer hypothetical.
The Business Impact of BAS Cyber Breaches
For building owners and operators, the consequences of a BAS cyberattack extend far beyond IT concerns. Impacts include:
- Safety Risks – In hospitals or high-rises, disrupted systems can put lives at risk.
- Financial Losses – Downtime leads to lost tenant productivity, higher energy costs, and potential penalties.
- Reputation Damage – Tenants and occupants expect safety, security, and reliability. A publicized cyberattack undermines trust.
- Compliance Concerns – With new regulations like NIS2 in the EU and NIST Cybersecurity Framework 2.0 in the U.S., building owners may face legal or financial penalties for failing to secure BAS.
Moving from Awareness to Action
Recognizing the risk is the first step. To move toward resilience, facility managers and executives should:
- Assess Current BAS Security Posture – Identify which systems use legacy protocols, default passwords, or lack authentication.
- Apply Zero Trust Principles – Replace implicit trust with “never trust, always verify” at the device level.
- Secure Legacy Devices – Rather than replacing costly infrastructure, apply solutions like DOME™ by Veridify Security, which provides cryptographic authentication and encryption for existing devices.
- Integrate BAS Into Cybersecurity Strategy – BAS should not sit outside the scope of IT/OT security planning and monitoring.
- Prepare for Compliance Requirements – Stay ahead of new regulations by aligning BAS security practices with NIST CSF, DoD Zero Trust, and EU NIS2 guidelines.
Conclusion
Building automation systems are a new frontier for cybercriminals. Once considered too obscure or isolated to be targeted, BAS now represents a direct pathway to disruption, extortion, and network compromise. As connectivity grows, the risks increase.
By adopting device-level Zero Trust security, securing legacy protocols, and preparing for regulatory compliance, building owners and facility managers can transform BAS from the weakest link into a last line of defense.
Key Takeaways
- BAS is now a top cyber target due to its operational importance and connectivity to enterprise IT systems.
- Legacy protocols and devices often lack encryption, authentication, or strong passwords, leaving systems exposed.
- Real-world incidents — from school HVAC shutdowns to water utility breaches — show attackers are actively exploiting BAS vulnerabilities.
- Impacts extend beyond IT to include safety, financial losses, compliance risks, and reputational damage.
- Zero Trust at the device level ensures mutual authentication, encrypted communications, and protection against unauthorized devices or firmware.
- Veridify’s DOME™ platform delivers this protection without replacing legacy infrastructure, while also preparing BAS for future threats like quantum computing.