Zero Trust – A Virtual Air Gap for OT Security

Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making, and more.
Operational Technology Air Gap Security Risks
The reality of today’s manufacturing facilities, industrial plants, and buildings is that there are multiple ways to get by air gaps. Below are several methods and here are some advanced methods.
| Remote Access | Remote access is a widely used method to enable operating efficiency by allowing employees and contractors to have remote access to operational systems. Enabling remote access is sort of the opposite of air-gapping but is more secure than having non-secure access. Some risks for remote access include password sharing, access from infected computers, or lack of software updates. |
| USB Sticks | Everyone loved USB sticks 10 years ago as a simple way to store and transport data. Today, USB sticks are well known vehicles for cyber breaches. They can be intentionally “planted” as lost items in a parking lot, received as promotional items, or accidentally infected at home. If they are plugged in to an air-gapped computer they can create significant cybersecurity risks. Employee training can help, along with disabling USB ports on air-gapped systems. |
| Smartphones | Smartphone penetration in developed countries is over 80% of the population. Smartphones bring unsecure access directly into a secure environment in the form of mobile access, Wi-Fi hotspots, microphones, cameras, GPS location, and other sensors. As a result, air-gapped computers can be directly connected to the Internet by unsuspecting employees creating an attack vector for prospective intruders. |
| KVM switches | KVM switches are typically used to share a single keyboard, mouse, and monitor with multiple CPUs. They provide a convenient way to use peripherals with one computer and then switch them to use with another computer. This provides spaces savings, are more ergonomic and efficient than having multiple keyboards, etc. and help to keep workspaces more organized. Regular KVM switches can be compromised where electrical activity from one side can be detected on the other side and used to gather intelligence that can be used for a cyberattack. To solve this problem, secure KVM switches should be NIAP-certified. |
Re-Creating the “Air Gap” with Zero Trust Security
Zero Trust security is a cybersecurity approach that challenges the traditional “trust but verify” model of network security. In the traditional model, once a user or device gains access to a network, they are often trusted to move freely within it, relying on perimeter defenses like firewalls to keep threats out. Zero Trust, on the other hand, is based on the principle of “never trust, always verify.” It assumes that threats could already be inside the network and that trust should not be automatically granted to anyone, whether inside or outside the network perimeter. Instead, Zero Trust emphasizes continuous verification and strict access controls.
For operational technology networks (i.e. ICS, SCADA, Modbus, BACnet, etc.) that are no longer air-gapped, implementing a zero trust framework can provide improved security in the event of a breach in the cyber perimeter.
Implementing Zero Trust for Existing OT Devices
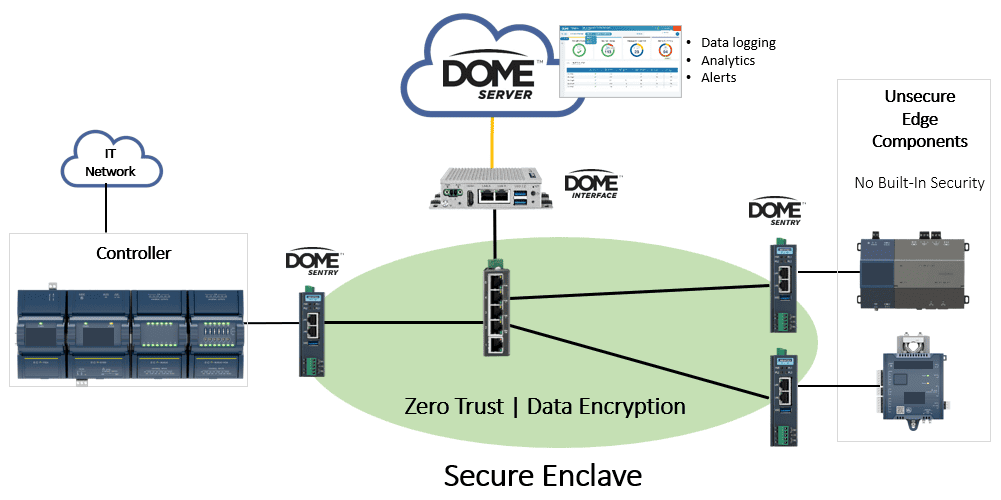
OT devices typically have long lifecycles and millions of devices in the field today are not able to be upgraded. Fortunately, it’s possible to build a security overlay to create a secure enclave using a zero trust framework. Veridify’s DOME platform utilized DOME Sentry devices that can be placed in front one or more OT devices to provide authentication and data encryption. In the case of someone listening on the network they will not be able to connect with other devices or learn anything from the data traffic.
Contact us or learn more about DOME for critical applications:
Industrial Automation (Industrial Control Systems / SCADA)
Building Automation (and Smart Buildings)