Zero Trust for OT Security – Shields Up vs Damage Report
In the original and newer Star Trek episodes and movies, the captain would order “shields up” or “raise shields” prior to an attack to prevent damage to the USS Enterprise. The shields were some sort of force field of which the physics is never fully described. During or after an attack the captain would request a damage report to find out what damage was inflicted to the ship.
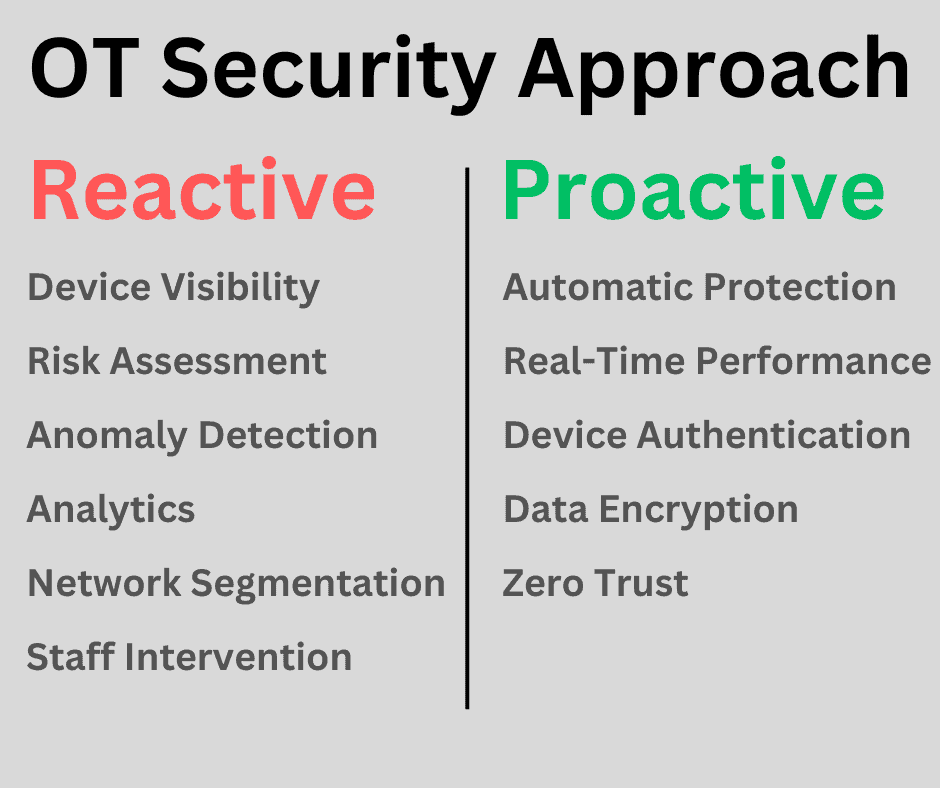
Reactive OT Security
For OT security, there are many tools and SaaS solutions on the market today that provide “damage reports” after a cyberattack has occurred. These are network monitoring tools that identify asset inventory, look for anomalies, provide network segmentation, and enable remediation. These are valuable and useful capabilities for identifying and limiting damage from an intrusion or cyberattack after it has occurred. However, they are reactive solutions. This is similar to a security alarm system detecting motion and alerting after someone is already inside.
Proactive OT Security
Another way to provide OT security is with a proactive approach that involves measures to stop damage while an intrusion or attack is occurring. Shields provide real-time protection against attacks. The Romans, Greeks, and many other armies used shields, the stone walls of castles were shields, and the armor on modern tanks are shields.
Zero Trust for OT Security
Zero Trust is the new, modern shield for IT and OT applications, data, and equipment. Zero Trust is based on the premise that all users or devices are untrusted unless specifically authenticated to access a specific resource such as data, a server, or OT device. Zero Trust is a foundational component for proactive security that delivers automatic and real-time protection that stops damage or data loss from occurring.
DOME: A “shields up”, proactive, device-level approach to endpoint OT security
Network intrusions may occur for a lot of reasons, and Veridify Security provides the “shields up” equivalent for protecting endpoint devices and equipment used in building automation, industrial automation / ICS, and operational technology (OT) networks. More than just monitoring (i.e. a damage report), Veridifiy’s DOME™ platform protects endpoint devices and stops cyberattacks in real-time (i.e. a shield). DOME works with existing devices and protocols so there’s no need to replace or upgrade devices, or change network topology. DOME creates a security overlay, or secure enclave, powered by a zero trust framework.
The elements of DOME include:
- Device management
- Secure firmware updates
- Authentication for all devices
- Secure and encrypted communications
- Security dashboard
- DOME Sentry security gateways
DOME security software can be embedded into new devices from any manufacturer, and the DOME Sentry is used to protect existing and legacy devices. Even better, unlike the shields on the Enterprise which could eventually be worn down, DOME does not wear down from repeated attacks.
Click these links to learn more or contact us to schedule a call.