Zero Trust Security for Legacy OT Devices
How Can Zero Trust Security be Added to Legacy OT Devices?
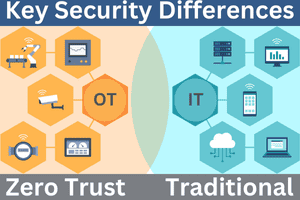
Implementing Zero Trust Security in legacy OT devices, systems, and equipment requires balancing modern security principles with the limitations of aging infrastructure.
Key Challenges with Legacy OT Systems
- Outdated Protocols: Many legacy devices use insecure protocols (e.g., Modbus, DNP3) lacking data encryption or authentication.
- Missing Security Features: Hardcoded credentials, no MFA support, and limited logging capabilities.
- Hardware limitations: Legacy OT devices, that may still have years of operational capability, may have insufficient processing speed and memory in order to implement modern security methods including authentication and encryption.
- Operational Risks: Downtime or disruptions from security updates could halt critical processes.
There are three potential options to consider for adding device-level zero trust:
| Method | Pros | Cons |
| Device Replacement |
|
|
| Software -Defined Networking |
|
|
| Security Overlay |
|
|
Network monitoring solutions that detect anomalies are not capable of providing zero trust or encrypting data traffic, and were intentionally excluded from the table above.
DOME™ – Zero Trust OT Security Solution
DOME, by Veridify Security establishes a Zero Trust architecture, creating a “secure enclave” that ensures all devices within an OT environment are authenticated and protected. Through advanced cryptographic techniques and blockchain-based credentialing, DOME secures industrial controls, building automation systems, and other networked devices, eliminating the need for extensive cybersecurity expertise during deployment.
Key features of the DOME platform include:
- Zero Trust: Network, device, and packet authentication with a NIST-compliant zero trust framework.
- Device-Level Security: Prevents unauthorized access and ensures secure data exchange.
- Zero-Touch Provisioning: Automates device authentication and setup including configuration and creation, distribution, and renewal of certificates, minimizing human error.
- End-to-End Encryption: Encrypts all network traffic, eliminating the risk of eavesdropping or data tampering.
- Multi-Protocol Protection: Secures devices using numerous industrial TCP/IP protocols including EtherNet/IP, Modbus TCP, DNP3, HART-IP, OPC UA, BACnet/IP, SNMP, H.264 encoded video and more.
- Crypto-Agility: supports various cryptographic methods and future-proofs security infrastructure with support for quantum-resistant encryption.
- Post-Quantum Security: Supports three post-quantum cryptographic algorithms identified by NIST for standardization, FIPS 203 (ML-KEM), FIPS 204 (ML-DSA), and FALCON, when it is formally published. This feature will ensure protection against quantum computing threats.
- Secure Firmware Updates: Secure firmware delivery to support up-to-date security patches.
- Supply Chain Security: Establishes a blockchain-based ownership pedigree for devices, preventing unauthorized modifications or counterfeit components.
- Enterprise Support: Access to enterprise services, such as DNS, SMTP, and RADIUS, for protected devices without requiring these services to be located within the secure enclave.
- Real-time protection: Blocks attempted cyberattacks against unauthorized (unauthenticated) devices
Zero Trust and Secure Enclave Implementation
A fundamental pillar of DOME’s architecture is its Zero Trust framework. In this model, devices are considered untrustworthy until they are authenticated, ensuring that only verified devices can communicate within the secure enclave. This approach effectively neutralizes threats from rogue devices, unauthorized network intrusions, and insider attacks.
Proactive Cyber Threat Prevention
Unlike traditional security solutions that rely on anomaly detection and reactive incident response, DOME proactively blocks unauthorized access at the packet level. By embedding security directly into the network infrastructure, DOME eliminates vulnerabilities commonly exploited by attackers, such as unsecured legacy devices and unencrypted communication channels.
Quantum Computing Cybersecurity Readiness
With the advent of quantum computing, traditional encryption methods face increasing risks. DOME addresses this challenge with its DOME PQ Sentry, which integrates post-quantum cryptographic protection aligned with NIST’s recommendations. This ensures long-term cybersecurity resilience for new and legacy automation controls. The system is designed to be crypto-agile, enabling seamless updates to future-proof security.
Deployment and Use Cases
DOME’s flexible deployment model allows organizations to implement security across diverse environments, including:
- Industrial and Manufacturing: Protecting actuators, motors, valves, robots, and other machinery
- Commercial and Industrial Buildings: Protecting HVAC, lighting, elevators, life safety, and access control systems
- Critical Infrastructure: Enhancing security in power plants, water treatment facilities,
- and transportation networks.
- Defense and Government Facilities: Meeting stringent security requirements with post-quantum cryptography and blockchain-based device authentication.
Conclusion
DOME represents a paradigm shift in OT security, offering an easy-to-deploy, scalable, and resilient cybersecurity solution. By integrating Zero Trust principles, blockchain-based device verification, and advanced encryption, DOME ensures long-term protection for connected devices in industrial and commercial environments. The introduction of post-quantum cryptographic protections further solidifies DOME as a future-ready solution for evolving cyber threats. Organizations seeking to fortify their OT networks against both classical and quantum computing threats will find DOME to be a robust and comprehensive security platform.
—
Blog Post Summary – All of our recent posts listed on one page