Zero Trust for OT Security: The Last Line of Defense
Quick Summary
Traditional firewalls were never designed to meet the unique security needs of Operational Technology (OT) environments. While they are effective at blocking outside threats, once an attacker breaches the perimeter, devices inside remain vulnerable. Real-world incidents like Colonial Pipeline, Triton malware, and ransomware in building automation highlight how attackers exploit insecure OT protocols and lateral movement inside networks. Veridify’s DOME™ platform closes these gaps by embedding Zero Trust principles directly at the device level. Through cryptographic authentication, encrypted communications, and protocol-agnostic security, DOME provides the essential last line of defense that firewalls cannot deliver.
Introduction
Traditional IT security solutions, such as firewalls, were designed for enterprise networks where threats typically originate from outside the perimeter. Operational Technology (OT) environments, including industrial control systems, building automation, and critical infrastructure, have very different requirements. Devices must communicate reliably in real time; many protocols were never designed with security in mind, and “air gaps” no longer exist in practice. In this setting, Veridify’s DOME™ Zero Trust platform protects at the device level, addressing gaps that perimeter-based firewalls cannot cover, and providing a last line of defense when a firewall breach occurs.
Firewalls in OT
Firewalls enforce security policies at network chokepoints. They examine packet headers and sometimes payloads to allow or block traffic based on rules. While effective in preventing unauthorized external access, firewalls face significant challenges in OT networks:
- Firewalls assume an “inside versus outside” trust model, where internal devices are trusted by default, along with internal traffic that has passed through the firewall.
- They provide limited visibility into device identity; a firewall cannot confirm if a programmable logic controller (PLC) or building controller is authentic or spoofed.
- They struggle with OT protocols (e.g., BACnet, Modbus), which were not designed with security in mind and may require fragile custom rules.
- Once an attacker gains access inside the OT perimeter, firewalls offer little protection against lateral movement between devices.
Real-World Failures of Firewall-Only Approaches
- Colonial Pipeline (2021): A single compromised VPN credential allowed attackers to move inside the network. Firewalls at the perimeter were bypassed, and once inside, attackers shut down operations, leading to fuel shortages across the U.S. East Coast1.
- How DOME Helps: Every device-to-device communication in DOME requires mutual authentication and encryption. A stolen credential alone would not enable an attacker to issue commands or move laterally across the OT network.
- Triton/Trisis Malware (2017): Attackers targeted a safety instrumented system (SIS) at a Saudi petrochemical facility. Although perimeter defenses existed, malicious code was injected into critical controllers once the attackers gained a foothold inside2.
- How DOME Helps: Controllers provisioned with DOME would only accept commands from authenticated and authorized devices. An attacker’s attempt to impersonate an engineering workstation would be blocked at the cryptographic level.
- Building Automation Ransomware (2019–2023): Multiple cases have been documented in which attackers exploited insecure OT protocols, such as BACnet, to manipulate HVAC and building management systems. Even when firewalls were in place, misconfigurations and weak segmentation allowed lateral movement and control disruption3.
- How DOME Helps: DOME secures all BACnet or Modbus communications with strong keys and certificates, preventing spoofing or unauthorized access even if the underlying protocol is insecure.
These examples highlight a common theme: firewalls protect the perimeter, but once attackers breach or bypass that perimeter, devices remain unprotected.
DOME in OT
DOME was built specifically for OT and IIoT environments, embedding Zero Trust and cryptographic enforcement at the device level:
- Device Identity and Authentication: Every device is provisioned with unique ephemeral keys and certificates, ensuring that only verified devices can communicate securely.
- Encrypted Communications: All sessions between devices are protected, preventing spoofing, interception, or man-in-the-middle attacks.
- Protocol-Agnostic Security: Because DOME operates at the device and session layer, it secures any OT protocol transparently without requiring protocol-specific inspection.
- Scalability: Designed to manage thousands of devices, DOME automates provisioning, key management, and in-field cryptographic upgrades, including post-quantum readiness.
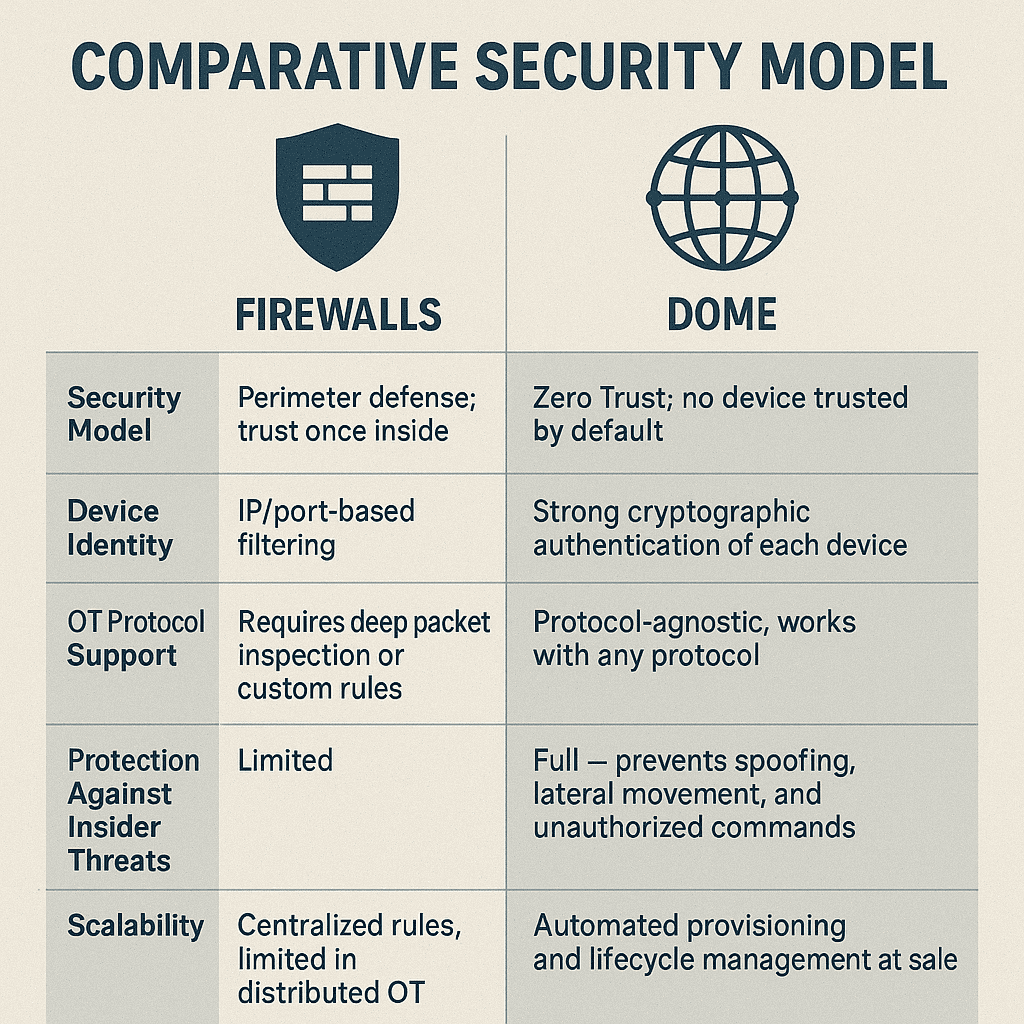
Comparative Security Model
Aspect |
Firewalls |
DOME |
| Security Model | Perimeter defense; trust once inside | Zero Trust; no device trusted by default |
| Device Identity | IP/port-based filtering | Strong cryptographic authentication of each device |
| OT Protocol Support | Requires deep packet inspection or custom rules | Protocol-agnostic, works with any protocol |
| Protection Against Insider Threats | Limited | Full — prevents spoofing, lateral movement, and unauthorized commands |
| Scalability | Centralized rules, limited in distributed OT | Automated provisioning and lifecycle management at scale |
Defense-in-Depth
Firewalls remain important for securing the perimeter between IT and OT environments, thereby preventing external attackers from gaining entry. However, they cannot ensure the trustworthiness of the devices inside the OT network. DOME provides the missing layer: a last line of defense that provides device-level Zero Trust protection and prevents unauthorized devices or compromised controllers from communicating. Together, firewalls and DOME form a complementary, defense-in-depth strategy tailored to the unique demands of OT security.
Key Takeaways
-
Firewalls alone are insufficient in OT: They assume trust inside the perimeter and offer limited protection against insider threats or compromised devices.
-
Real-world attacks prove the risks: Colonial Pipeline, Triton, and building automation ransomware bypassed perimeter defenses to cause operational disruption.
-
DOME enables Zero Trust for OT: Every device must authenticate cryptographically, and all communications are encrypted, regardless of protocol.
-
Stronger insider threat protection: DOME prevents spoofing, lateral movement, and unauthorized commands even after a breach.
-
Scalable and future-ready: Automated provisioning and cryptographic agility, including post-quantum readiness, make DOME practical for large OT and IIoT deployments.
-
Defense-in-depth strategy: Firewalls still protect the perimeter, but DOME ensures device-level security as the last line of defense.
Footnotes
- U.S. Department of Homeland Security, “Colonial Pipeline Cyber Incident,” 2021; CISA & FBI advisories.
- FireEye/Mandiant, “Attackers Deploy TRITON Malware Against Safety Systems,” 2017.
- Honeywell, “Building Automation Systems Under Attack,” 2020; various ICS-CERT advisories.