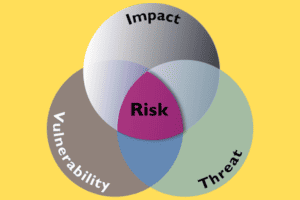
Cybersecurity Challenges in Retrofitted Smart Buildings

Key Points
-
Legacy Systems Are Inherently Vulnerable: Most retrofitted buildings rely on outdated OT devices and insecure protocols (like BACnet and Modbus) that lack basic cybersecurity features such as encryption and authentication.
-
Integration Increases Risk: Retrofitting often connects legacy OT systems to modern IT networks without proper segmentation, exposing buildings to lateral movement and cyberattacks.
-
Real-World Threats Are Emerging: High-profile incidents demonstrate how attackers can exploit old systems in smart buildings, escalate control, and demand ransom by disrupting critical infrastructure.
-
Mitigation Requires Multi-Layered Strategies: Key defenses include hybrid network segmentation, legacy device hardening, phased modernization, anomaly detection, and zero trust implementation tailored for building automation systems.
-
Security Must Lead Modernization: As retrofitting accelerates globally, organizations must prioritize proactive cybersecurity—including risk assessments and compliance—before integrating smart technologies into aging infrastructure.
As cities worldwide push to modernize aging infrastructure, older commercial buildings are increasingly being retrofitted with smart technologies like IoT sensors, cloud-based management systems, and AI-driven automation. While these upgrades enhance energy efficiency and tenant experiences, they introduce a critical challenge: securing legacy systems never designed for connectivity. This article explores the unique risks of retrofitting and actionable strategies to protect these hybrid environments.
The Rise of the Retrofitted Smart Buildings
Roughly 75% of commercial buildings in the U.S. were constructed before 2000, many relying on decades-old operational technology (OT) like HVAC controls, elevators, and fire safety systems. Retrofitting these systems with smart tech often involves bridging legacy, insecure protocols (e.g., BACnet, Modbus) with modern IP-based networks—a process that inadvertently exposes vulnerabilities. For example, ShadowServer’s dashboard reveals about 100,000 exposed legacy devices globally, many in retrofitted buildings. These legacy systems, now connected to the internet, become low-hanging fruit for cyberattacks.
Why are Legacy Building Management Systems a Cybersecurity Challenge?
Retrofitted smart buildings face three core vulnerabilities:
- Outdated Protocols and Hardware
Many legacy devices lack authentication and encryption, use default credentials, or depend on deprecated communication protocols. Attackers exploit these weaknesses to infiltrate networks. - Poor Network Segmentation
Retrofitting often integrates OT and IT systems without proper isolation. A 2023 study found that 58% of smart buildings have OT networks accessible from corporate Wi-Fi, enabling lateral movement for attackers. - Limited Patchability
Legacy devices frequently run outdated and unsupported software or firmware. Updating them may require costly hardware replacements, leaving vulnerabilities unaddressed for years.
Real-World Risks: When Old Meets New
Consider a hypothetical attack on a retrofitted office tower:
- Phase 1: Hackers exploit an unpatched vulnerability in a 1990s-era HVAC controller connected to a new IoT management platform.
- Phase 2: They pivot to the building’s access control system, locking tenants out during business hours.
- Phase 3: The threat actors gain control of backup generators or other control system, require a ransom and threaten a total shutdown unless a payment is made.
Such scenarios are plausible. In 2021, a hacking incident targeted an HVAC vendor that provides HVAC systems to several Boston area hospitals.
Strategies for Securing Retrofitted Smart Buildings
- Hybrid Network Segmentation
- Isolate legacy systems using VLANs or hardware firewalls.
- Deploy “air-gapped” networks for critical OT devices, allowing data replication to modern systems without direct connectivity.
- Deploy a zero trust solution for protecting the BAS/BMS.
- Legacy Device Hardening
- Replace default credentials and disable unused services.
- Use protocol gateways to encrypt legacy communications (e.g., wrapping Modbus in TLS).
- Add an overlay security system that implements authentication and data encryption
- Phased Modernization
- Prioritize upgrades for systems with the highest risk (e.g., fire alarms, elevators).
- Implement middleware to bridge old and new systems securely during transitions.
- Continuous Monitoring for Anomalies
- Deploy intrusion detection systems (IDS) tailored to OT traffic patterns.
- Monitor for unusual activity, such as a 20-year-old boiler controller suddenly transmitting data to an overseas IP.
- Third-Party Risk Management
- Vet contractors retrofitting systems for compliance with IEC 62443 or NIST SP 800-82 standards.
- Ensure vendors remove backdoor accounts after project completion.
- Incident Response Planning for Legacy Systems
- Develop manual override procedures for critical OT devices (e.g., physical switches for elevator controls).
- Conduct tabletop exercises simulating attacks on retrofitted infrastructure.
The Role of Risk Assessments in Retrofitting
A thorough risk assessment for retrofitted buildings should:
- Map all legacy and modern systems, noting interdependencies.
- Identify “single points of failure” where outdated tech interacts with new platforms.
- Test legacy devices for vulnerabilities using tools like Shodan or Censys, which can reveal exposed BACnet or Modbus interfaces.
Looking Ahead: Balancing Innovation and Security
The retrofit trend will continue, driven by energy management and security goals. However, securing these buildings requires a shift in mindset:
- Regulatory Pressure: New standards like the EU’s Cyber Resilience Act may mandate stricter OT security in retrofits.
- AI-Driven Solutions: Local agents could detect anomalies in legacy system behavior, providing an extra layer of defense.
Retrofitted buildings with updated and smart technology represent a transition from the past to the future. While integrating old systems with cutting-edge tech is essential for progress, it demands proactive cybersecurity measures. By adopting tailored strategies—hybrid segmentation, phased upgrades, zero trust—organizations can protect these environments without sacrificing innovation. In the race to modernize, security must be the foundation, not an afterthought.
—
DOME: Cybersecurity for Smart Buildings (4-min demo)
—
Blog Post Summary – All of our recent posts listed on one page