Zero Trust Security for Microgrids and Energy Control Systems
Key Points
-
Growing Cyber Risk in Microgrids: The distributed nature, two-way data flows, and device diversity in microgrids greatly expand the attack surface, making traditional perimeter-based security insufficient.
-
Limitations of Legacy Security: Older “verify then trust” models lack device-level authentication/encryption, leaving systems vulnerable if an insider device is compromised and failing to protect at Purdue Model Level 0.
-
DOME’s Zero Trust Architecture: Veridify’s DOME platform creates a secure enclave from Level 0 through Level 2, authenticating every device before communication and blocking unauthorized access proactively at the packet level.
-
Advanced and Future-Proof Protection: DOME uses blockchain-based credentialing, post-quantum cryptography, and protocol compatibility to secure both legacy and new devices without requiring deep cybersecurity expertise.
-
Flexible Deployment Options: The solution includes DOME Server, Interface Appliance, Sentry™ gateway, and Client software, supporting major industrial protocols (BACnet/IP, Modbus TCP, DNP3, OPC UA, etc.) for cost-effective, scalable microgrid security.
Microgrid Security
As critical infrastructure operators adopt increasingly complex OT networks to support distributed energy resources, microgrids, and water treatment systems, the attack surface for cyber threats continues to grow. Legacy perimeter-based security is no longer adequate to defend against persistent and advanced threats. A modern, Zero Trust approach is required to ensure that only explicitly authorized entities can communicate across OT environments, while continuously monitoring and mitigating threats in real time.
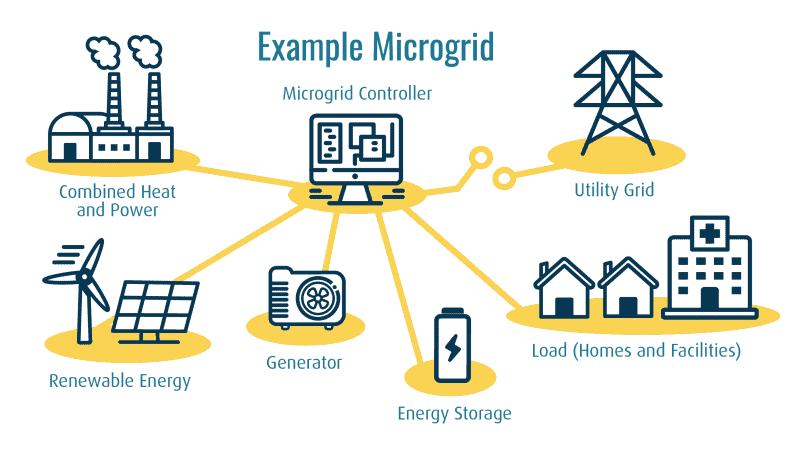
By enabling continuous and self-regulating operation of critical infrastructure in the event of disruptions to the broader power distribution system, microgrids comprise a critical component to enhance energy independence and resilience while reducing energy costs. However, the same elements that make a microgrid resilient (i.e., distributed control and intelligence, enabled by two-way data flows) also greatly increase the cyber-attack surface, making these networks uniquely vulnerable to cyber-attack.
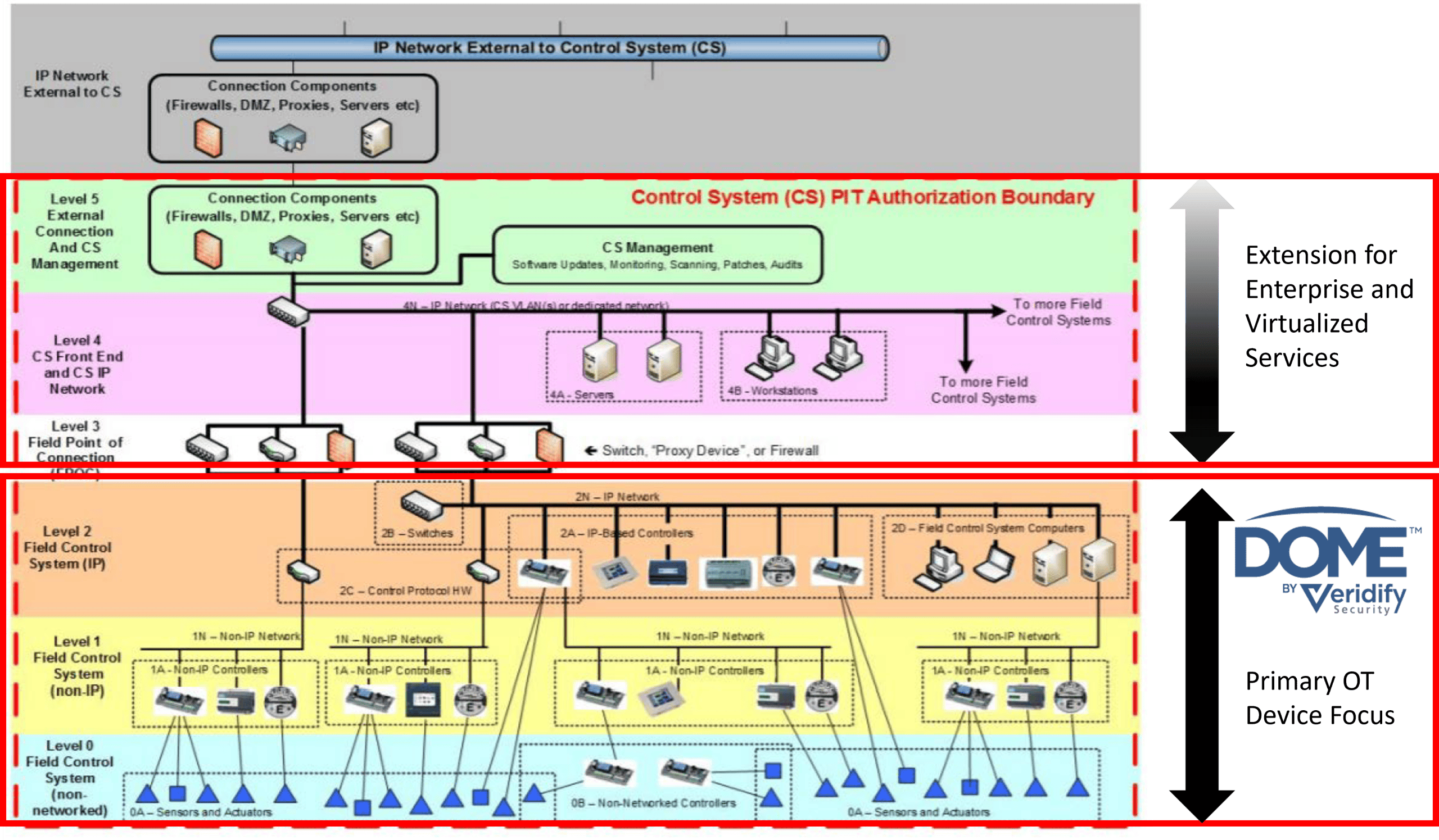
Microgrids are typically comprised of a combination of Distributed Energy Resources (DERs), Facility Related Control Systems (FRCS), and one or more dedicated microgrid control platforms, which is responsible for matching electricity supply and demand in real-time. A legacy approach to managing microgrid cybersecurity seeks to establish a secure perimeter around these devices, allowing only trusted devices inside the perimeter (a “verify then trust” approach). However, these devices lack authentication and encryption. This approach is brittle since a compromised device inside the secure perimeter can compromise the security of the entire network. While some technology solutions target higher levels of abstraction in the Purdue Model Framework for Industrial Control Systems and Cybersecurity Segmentation, none address extending zero trust to the device level (Level 0), hardening the devices, or encrypting data packets from these devices. Perimeter security and network monitoring can reduce risk and dwell time, but do not enable zero trust at the device level and do not stop attacks.
DOME: Zero Trust Security for Microgrids
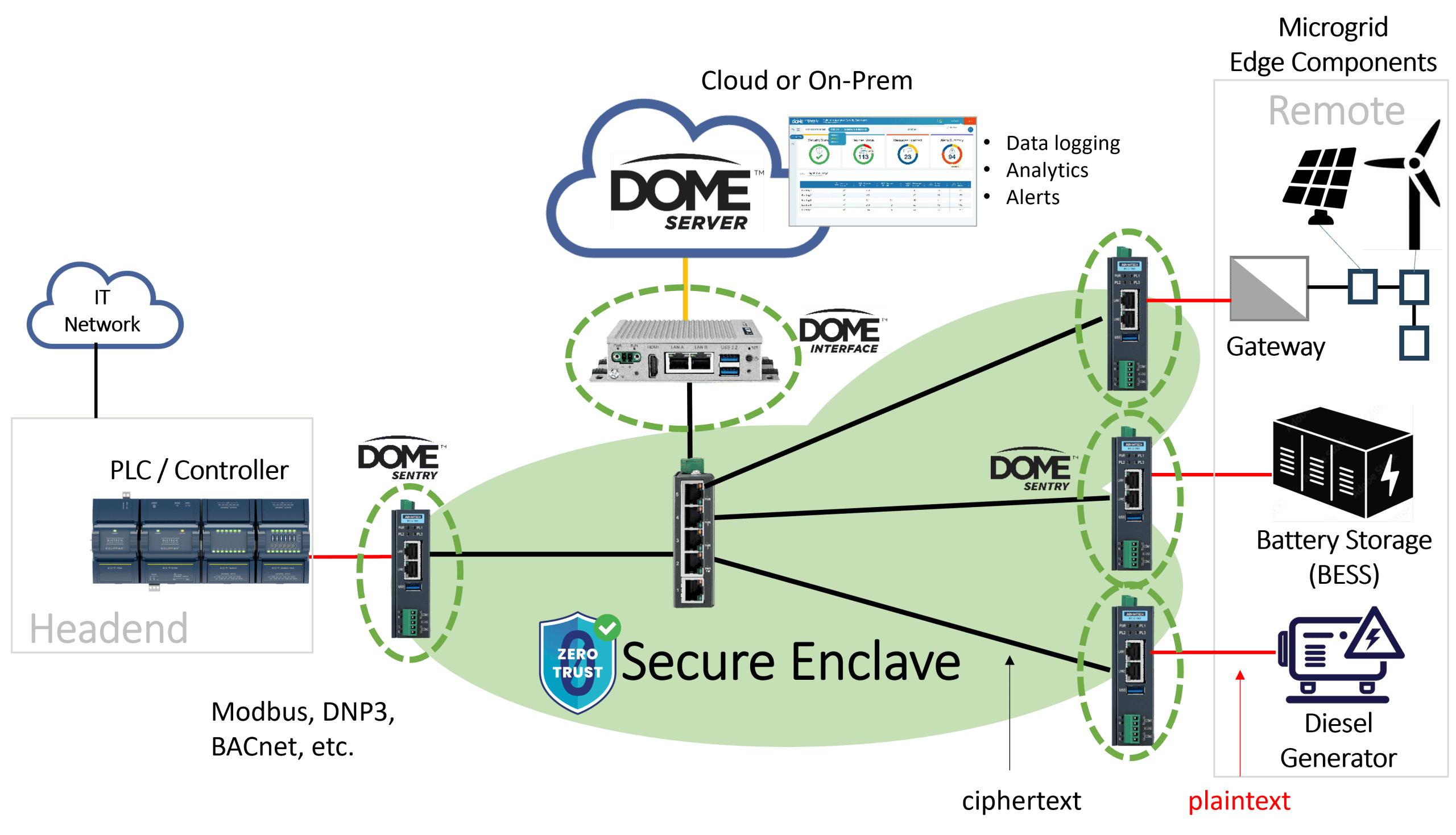
DOME, by Veridify Security, is a modern solution for securing and managing microgrids. The DOME platform uses a combination of security gateways and/or embedded authentication protocols to establish a Zero Trust architecture, creating a “secure enclave” that ensures all devices within an Operational Technology (OT) environment are authenticated and protected. Through advanced cryptographic techniques and blockchain-based credentialing, DOME secures industrial controls (ICS), building automation systems (BAS), facility related control systems (FRCS), and other networked devices, eliminating the need for extensive cybersecurity expertise during deployment.
Compatible with major controls vendors and protocols, DOME was built on a foundation of compatibility with upgrade paths for both new and existing microgrid platforms.
The DOME Platform establishes a Zero Trust architecture from Level 0 (device) through Level 2 (IP-enabled Field Control Systems), creating a “secure enclave” that ensures all devices within the Operational Technology (OT) environment are authenticated and protected. Within the Zero Trust architecture, devices are considered untrustworthy until they are authenticated, ensuring that only verified devices can communicate within the secure enclave. Moreover, unlike traditional security solutions that rely on anomaly detection and reactive incident response, DOME proactively blocks unauthorized access at the packet level. By embedding security directly into the network infrastructure, DOME eliminates vulnerabilities commonly exploited by attackers, such as unsecured legacy devices and unencrypted communication channels. Through advanced cryptographic techniques and blockchain-based credentialing, DOME secures industrial controls, building automation systems, and other networked devices, eliminating the need for extensive cybersecurity expertise during deployment. In addition, the proposed solution extends and future-proofs existing zero-trust concepts by implementing post-quantum security techniques.
DOME Components
The DOME platform integrates the following core components into a multi-layered security approach: (1) DOME Server for system/credential management and system-wide information, analytics and alerts that can be hosted in the Cloud or locally; (2) the DOME Interface Appliance for onsite system management, credential/token authentication, and logging; and (3) the DOME Sentry™ a gateway appliance that can be installed in an existing system and immediately provide protection to installed devices, along with site preparation and installation tools. Alternatively, the DOME Client offers a software-based security solution that can be embedded in OEM devices for native cybersecurity protection. The DOME Sentry integrates post-quantum cryptographic protection aligned with NIST’s recommendations,
This approach enables organizations to secure existing infrastructure without costly hardware overhauls. The solution is highly adaptable, supporting various industrial protocols, including BACnet/IP, Modbus TCP, DNP3, OPC UA, SMTP, and now extends protection to complementary non-BACnet protocols, such as Tridium’s Niagara Framework.
Key features of the DOME platform include:
- Device-Level Security: Prevents unauthorized access and ensures secure data exchange.
- Zero-Touch Provisioning: Automates device authentication and setup, minimizing human error.
- End-to-End Encryption: Encrypts all network traffic, eliminating the risk of eavesdropping or data tampering.
- Multi-Protocol Protection: Secures both Industrial protocols, BACnet/IP and TCP/IP traffic at the device level of an Operational Technology (OT) Network, providing comprehensive cybersecurity for buildings with mixed protocol environments.
- Crypto-Agility: Future-proofs security infrastructure with support for quantum-resistant encryption.
- Post-Quantum Security: Supports three post-quantum cryptographic algorithms identified by NIST for standardization, FIPS 203 (ML-KEM), FIPS 204 (ML-DSA), and FALCON (when it is formally published). This feature will ensure protection against quantum computing threats.
- Secure Firmware Updates: Ensures devices maintain up-to-date security patches.
- Supply Chain Security: Establishes a blockchain-based ownership pedigree for devices, preventing unauthorized modifications or counterfeit components.
[microgrids], [zero trust], [energy control systems]
—
Blog Post Summary – All of our recent posts listed on one page