Posts by Veridify Security
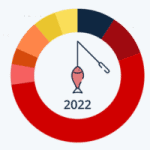
Share of Worldwide Cyber Attacks by Type 2022
October is Cybersecurity Awareness Month. While Veridify specializes in cybersecurity for Building Automation, Industrial Controls Systems (ICS/.SCADA), and Critical Infrastructure, we also share in raising awareness for everyone to improve their cybersecurity posture. As the data below indicates, the most prevalent form of cyber crime in 2022 was from phishing attacks. We all see this…
Read MoreBuilding Automation Systems, Smart Buildings, and 5 Ways to Make Them Cyber Secure
Watch this webinar replay of “Building Automation Systems, Smart Buildings, and 5 Ways to Make Them Cyber Secure” to learn about cybersecurity for buildings. Key Topics Buildings are becoming more connected and more at risk to cyberattacks. This webinar will address the following items: • Connected building trends • Building controls advancements and operating efficiencies…
Read MoreZero Trust – A Virtual Air Gap for OT Security
Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making,…
Read MoreZero Trust for OT Security – Shields Up vs Damage Report
In the original and newer Star Trek episodes and movies, the captain would order “shields up” or “raise shields” prior to an attack to prevent damage to the USS Enterprise. The shields were some sort of force field of which the physics is never fully described. During or after an attack the captain would request…
Read MoreZero Trust for OT Security – Overcoming Legacy Device Security Gaps and Technical Debt
The proliferation of interconnected Operational Technology (OT) devices in critical infrastructure and industrial sectors has ushered in new opportunities for increased efficiency and automation. However, this digital transformation also brings forth significant cybersecurity challenges. Perimeter security is not a sufficient solution and legacy devices and systems often lack robust security measures, leaving critical infrastructure vulnerable…
Read MoreModbus Security Issues and How to Mitigate Cyber Risks
Key Points Modbus Lacks Fundamental Security: Designed for isolated environments, Modbus protocols (especially Modbus TCP) lack encryption, authentication, access control, and integrity checks, making them highly vulnerable to cyberattacks. Common Vulnerabilities: Issues include default configurations, outdated firmware, absence of logging, susceptibility to replay, MitM, DoS, command injection, insider threats, and poor physical and network security.…
Read MoreProtecting Farms and AgTech from Cyberattacks
AgTech Overview Agricultural control systems, used for implementing precision agriculture, and part of the overall AgTech category, are used to manage and optimize farm operations through the use of technology. These systems have become increasingly sophisticated in recent years, utilizing sensors, drones, and other connected devices (IoT) to collect and analyze data on crops, soil,…
Read MoreCybersecurity threats to hospitals and healthcare facility building management systems
A recent cyberattack forced a healthcare organization to cancel non-emergency surgeries and send some emergency patients to other facilities. In another attack, a hospital took it’s critical systems offline, impacting patient safety, requiring less efficient care methods, which also increased labor demands. It’s still impacted two years later. Cyberattacks on hospital and healthcare facilities increased…
Read MoreZero Trust Security for Building Automation: What You Need to Know
Building automation systems (BAS) are becoming increasingly common in commercial buildings, providing centralized control of building operations, including HVAC, lighting, access control, elevators, and life safety systems. While these systems can increase energy efficiency and reduce costs, they also pose significant security risks. In recent years, there have been several high-profile attacks on building automation…
Read MoreCyberattacks on K-12 Schools and Higher Education
K-12 schools and universities are increasingly becoming targets for cyberattacks due to the valuable information they hold, such as student and staff personal data, financial information, and research data. Cyberattack statistics include: Proofpoint found that 90% of higher education institutions experienced at least one successful phishing attack in 2019. Malwarebytes found that the education sector…
Read More