Cybersecurity
AHR Expo 2025 Event Preview
Veridify Security will be exhibiting at the AHR Expo 2025 in Orlando at booth 1489. Verdify will be exhibiting a live demo of DOME™, a building automation cybersecurity platform that protects both new and existing building automation devices. The demo platform will showcase: DOME Sentry™ devices protecting an unprotected building thermostats and controller DOME Sentry…
Read MoreCybersecurity Awareness Month 2024
October is Cybersecurity Awareness Month 2024 Cybersecurity Awareness Month 2024 is a collaboration between government and private industry to raise awareness about digital security and empower everyone to protect their personal data from digital forms of crime. The Cybersecurity and Infrastructure Agency (CISA) and the National Cybersecurity Alliance partner to create resources and communications for…
Read MoreBuilding Automation Endpoint Protection Is Critical for Cybersecurity
Building automation systems (BAS), now highly-connected to the internet, have transformed how the infrastructure of residential, commercial, and industrial properties is managed and optimized. From heating, ventilation, and air conditioning (HVAC) systems to lighting, security, life safety, and power distribution, these systems are now smart, centralized, and increasingly automated. While this level of convenience and…
Read MoreModbus Vulnerabilities Used for Cyberattack on a Heating Utility
Heat and Hot Water Disrupted to over 600 buildings, about 100,000 people, for 48 Hours Cyberattack on a Heating Utility A cyberattack on a heating utility (also known as district heating) in the Ukrainian city of Lviv, the largest city in western Ukraine, in January 2024. The malware, named FrostyGoop, is one of the few…
Read MoreCybercrime Losses 2019-2023
The FBI released its annual Internet Crime Report for all complaints reported through its Internet Crime Complaint Center (IC3). From the report, cybercrime losses increased 21% from 2022. Cybercrime refers to criminal activities carried out using computers or the internet. These crimes can range from hacking and spreading malware to stealing personal or financial information, conducting…
Read MoreIncreasing Cyberattacks on Water Utilities
Water Utilities Cyberattacks Hacker groups from Russia, China, and Iran have all taken credit for recent cyberattacks on water utility companies in recent months, the EPA even warning smaller communities to take action. Water utility companies are on notice during federal inspections over the last year. Roughly 70% of them violated standards meant to prevent…
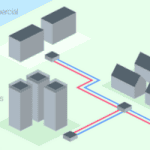
Read MoreBuilding Management System Cybersecurity Best Practices
A strong cybersecurity posture is essential for Building Management Systems to mitigate the risks associated with interconnected devices and systems. Building Management System Overview A Building Management System (BMS), also known as a Building Automation System (BAS) or Building Control System (BCS), is a computer-based control system that manages and monitors the mechanical, electrical, and…
Read MoreThe Role of Cybersecurity for IoT Devices
The Internet of Things (IoT) has revolutionized the way we live and work. With billions of connected devices, from smartphones to home appliances, building controls and industrial machinery, our world is more interconnected than ever before. However, this connectivity also brings with it significant security risks. Cybersecurity plays a crucial role in ensuring that data…
Read MoreMonetary Damage of Reported Cybercrime in the US from 2001-2022
Growth in Cybercrime Cybercrime is not just a threat to data and privacy; it also comes with a significant monetary cost. The monetary damage of reported cybercrime in the United States grew steadily from 2001-2017, and then accelerated starting in 2018. There was a year-over-year increase of around 50 percent from 2021 to 2022. Since…
Read MoreSmart Building Cybersecurity Best Practices
The true power of smart buildings lies in their ability to adapt and respond intelligently to the needs of occupants, enhancing comfort, efficiency, and sustainability. Understanding Smart Buildings Smart Buildings are structures equipped with a network of interconnected devices, sensors, and systems that collect and exchange data to optimize various aspects of building operations including…
Read More