OT Security
Zero Trust for OT Security: Cyber Defense Inside the Perimeter
Inside the Perimeter Defense is a Crucial Part of Defense in Depth for OT Security Firewalls for OT Security Perimeter Defense Firewalls are essential components of network security, acting as perimeter defenses that control incoming and outgoing network traffic based on predetermined security rules. However, they are not without their own set of potential security…
Read MoreModbus Vulnerabilities Used for Cyberattack on a Heating Utility
Heat and Hot Water Disrupted to over 600 buildings, about 100,000 people, for 48 Hours Cyberattack on a Heating Utility A cyberattack on a heating utility (also known as district heating) in the Ukrainian city of Lviv, the largest city in western Ukraine, in January 2024. The malware, named FrostyGoop, is one of the few…
Read MoreProtecting Building OT Systems from Cyber Threats
Operational Technology (OT) systems in buildings, which include HVAC, lighting, access control, and other critical infrastructure, are increasingly becoming targets for cyber threats. The rise in attacks on these systems underscores the importance of robust cybersecurity measures to protect them. Here’s a look at how to safeguard building OT systems from cyber threats. Understanding the…
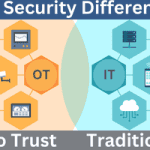
Read MoreKey Differences Between Zero Trust OT Security and Traditional IT Security
How is Zero Trust for OT Security Different from Traditional IT Security? Zero Trust for operational technology (OT) security differs significantly from traditional IT security models in several ways. Here are some key differences: Security Method Traditional IT Security Zero Trust OT Security Trust Model – Assumes that everything inside the network can be trusted.…
Read MoreImproving Cyber Physical Security
Introduction This is the podcast audio, highlights, and key insights from a Lunch and Learn session about the importance of improving cyber-physical security in building automation systems, highlighting the challenges and solutions in the industry. The event was hosted by KMC Controls. Podcast Audio – Improving Cyber-Physical Security Your browser does not support the audio…
Read MoreDNP3 Security Risks
DNP3 Cybersecurity Risks DNP3 (Distributed Network Protocol version 3) is a widely used communications protocol for industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. While DNP3 provides several features designed to enhance the reliability and efficiency of communication between control devices and data acquisition systems, it also poses certain security risks,…
Read MoreIncreasing Cyberattacks on Water Utilities
Water Utilities Cyberattacks Hacker groups from Russia, China, and Iran have all taken credit for recent cyberattacks on water utility companies in recent months, the EPA even warning smaller communities to take action. Water utility companies are on notice during federal inspections over the last year. Roughly 70% of them violated standards meant to prevent…
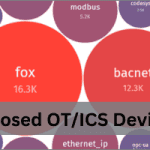
Read MoreIncreased Number of Cyber Exposed OT/ICS Devices
Exposed OT/ICS Devices Recent data from several tracking sources indicates there has been an increase in the number of public IP addresses with accessible devices using standard OT/ICS protocols – BACnet, Modbus, Fox, Ethernet/IP, S7, and more. Data from three different sources – Censys, ShadowServer, and Shodan – give insight into the number of publicly…
Read MoreZero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS/OT/SCADA)
Watch this webinar replay of “Zero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS /OT/SCADA)” to learn about applying zero trust security at the device level. This webinar addresses the following topics: ICS cybersecurity standards Existing ICS security approaches Zero Trust and device-level implementation Cybersecurity for existing ICS devices Zero Trust…
Read MoreZero Trust – A Virtual Air Gap for OT Security
Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making,…
Read More