Posts Tagged ‘ICS security’
Zero Trust: Reinforcing Security in Industrial Control Systems
As industrial control systems (ICS) become increasingly digitized, ensuring robust ICS security measures is paramount. In this article, we delve into the concept of Zero Trust and its potential to revolutionize the security landscape for industrial control systems. With cyber threats evolving in complexity and sophistication, traditional security measures are no longer sufficient. Zero Trust…
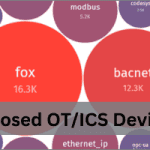
Read MoreIncreased Number of Cyber Exposed OT/ICS Devices
Exposed OT/ICS Devices Recent data from several tracking sources indicates there has been an increase in the number of public IP addresses with accessible devices using standard OT/ICS protocols – BACnet, Modbus, Fox, Ethernet/IP, S7, and more. Data from three different sources – Censys, ShadowServer, and Shodan – give insight into the number of publicly…
Read MoreZero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS/OT/SCADA)
Watch this webinar replay of “Zero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS /OT/SCADA)” to learn about applying zero trust security at the device level. This webinar addresses the following topics: ICS cybersecurity standards Existing ICS security approaches Zero Trust and device-level implementation Cybersecurity for existing ICS devices Zero Trust…
Read MoreZero Trust – A Virtual Air Gap for OT Security
Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making,…
Read MoreZero Trust for OT Security – Overcoming Legacy Device Security Gaps and Technical Debt
The proliferation of interconnected Operational Technology (OT) devices in critical infrastructure and industrial sectors has ushered in new opportunities for increased efficiency and automation. However, this digital transformation also brings forth significant cybersecurity challenges. Perimeter security is not a sufficient solution and legacy devices and systems often lack robust security measures, leaving critical infrastructure vulnerable…
Read More