Posts Tagged ‘Zero Trust’
Zero Trust Security for Legacy OT Devices
How Can Zero Trust Security be Added to Legacy OT Devices? Implementing Zero Trust Security in legacy OT devices, systems, and equipment requires balancing modern security principles with the limitations of aging infrastructure. Key Challenges with Legacy OT Systems Outdated Protocols: Many legacy devices use insecure protocols (e.g., Modbus, DNP3) lacking data encryption or authentication.…
Read MoreHow Zero Trust Enhances the Security of Building Control Systems
Zero Trust architecture significantly enhances the security of building control systems by implementing a comprehensive approach that assumes no implicit trust, regardless of the network location. This model is particularly beneficial for Building Automation Systems (BAS) due to their interconnected nature and vulnerability to cyberattacks. Key Benefits of Zero Trust for Building Control Systems…
Read MoreZero Trust for OT Security: Cyber Defense Inside the Perimeter
Inside the Perimeter Defense is a Crucial Part of Defense in Depth for OT Security Firewalls for OT Security Perimeter Defense Firewalls are essential components of network security, acting as perimeter defenses that control incoming and outgoing network traffic based on predetermined security rules. However, they are not without their own set of potential security…
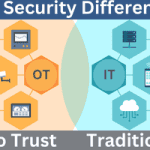
Read MoreKey Differences Between Zero Trust OT Security and Traditional IT Security
How is Zero Trust for OT Security Different from Traditional IT Security? Zero Trust for operational technology (OT) security differs significantly from traditional IT security models in several ways. Here are some key differences: Security Method Traditional IT Security Zero Trust OT Security Trust Model – Assumes that everything inside the network can be trusted.…
Read MoreEmbracing Digital Transformation – Zero Trust with Operational Technology
Embracing Digital Transformation – Zero Trust with Operational Technology Episode #175: In this episode titled “Embracing Digital Transformation – Zero Trust with Operational Technology” by Darren Pulsipher, Chief Solution Architect for Public Sector at Intel, interviews the CEO and Founder of Veridify Security Louis Parks. They discuss the unique problems with Operational technology networks that…
Read MoreZero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS/OT/SCADA)
Watch this webinar replay of “Zero Trust OT Security – Stopping Cyber Attacks on Industrial Control Systems (ICS /OT/SCADA)” to learn about applying zero trust security at the device level. This webinar addresses the following topics: ICS cybersecurity standards Existing ICS security approaches Zero Trust and device-level implementation Cybersecurity for existing ICS devices Zero Trust…
Read MoreZero Trust – A Virtual Air Gap for OT Security
Air-gapping computer and operational technology (OT) networks is a long-established method of protecting sensitive information and reducing the risk of operational disruption. A growing trend has been to provide connectivity from these networks to the Internet for remote monitoring and control, real-time data, data analysis, predictive maintenance, improving inventory and resource management, achieving faster decision-making,…
Read MoreZero Trust for OT Security – Shields Up vs Damage Report
In the original and newer Star Trek episodes and movies, the captain would order “shields up” or “raise shields” prior to an attack to prevent damage to the USS Enterprise. The shields were some sort of force field of which the physics is never fully described. During or after an attack the captain would request…
Read MoreZero Trust for OT Security – Overcoming Legacy Device Security Gaps and Technical Debt
The proliferation of interconnected Operational Technology (OT) devices in critical infrastructure and industrial sectors has ushered in new opportunities for increased efficiency and automation. However, this digital transformation also brings forth significant cybersecurity challenges. Perimeter security is not a sufficient solution and legacy devices and systems often lack robust security measures, leaving critical infrastructure vulnerable…
Read MoreZero Trust Security for Building Automation: What You Need to Know
Building automation systems (BAS) are becoming increasingly common in commercial buildings, providing centralized control of building operations, including HVAC, lighting, access control, elevators, and life safety systems. While these systems can increase energy efficiency and reduce costs, they also pose significant security risks. In recent years, there have been several high-profile attacks on building automation…
Read More